Come with me and you’ll be in a world of merging network infrastructures….
You know you are singing it now, right? You are welcome! Just a little gift from me to you. So, over the past few weeks I have been working my Zero Trust Network solution for my little corner of the world. Many ZTN strategies and best practices I have already implemented (despite my users complaining incessantly about having to use MFA… SUCK IT UP BUTTERCUP! I know you guys feel me on that statement.) Anyway, as the IT Manager, CISO, Support Guy and lately the resident LMR design n00b here at TX RX, I couldn’t help but think about the Cyber Security strategies I have implemented (are you starting to hate this term like “the cloud”? meh!). All these strategies are focused on normal “data” networks. But could the same strategies be applied to another type of network, like LMR or an OT network? (Yes, my fellow IT and network friends, there are whole other worlds out there!) For the most part, no. Don’t get me wrong, there are similarities but not many.

When we look at networks like OT (operational technology, think power facilities, manufacturing) and LMR these have been traditionally “Air-Gapped” (my network engineer friends know this). For those not in the know, “Air-Gapped” means is that these networks separated from a “data network”. They were islands unto themselves, completely independent of other networks and even the internet. But as these technologies evolved, it became more important that these networks be accessible for vendor support, upgrades, management, and data collection. And this, my friends, is where our lives just got a bit more complicated. Now we must deal with how to connect these networks to our data networks. We must learn how to not only manage our networks, but we also must start understanding the requirements of these other networks. They all have their own networking, security, and monitoring solutions. Now I can go into details and to be honest I love to talk about this stuff (hit me up on LinkedIn or email me, I am more than willing to chat). But the best advice I can give you is to talk to your controls engineer for OT or your radio engineer for LMR. You will find that these guys really truly understand their craft but are short on networking and security in most cases. But for this article I am going to focus more on security considerations on an LMR network.
As I mentioned, “Air-Gapping” is a great solution and was the way it was done for years. The LMR network is not connected to a traditional IP network, it will not be susceptible to viruses, hacking or other mischievous endeavors (well I suppose it cannot protect against human error). However, that is not the case anymore. Using a small municipality as an example, we usually had something like this:

The network is all contained in an LMR solution with no “IP networking”. Communication security (encryption) and filtering are handled by the handset vendors and the infrastructure equipment. Further, communication was mostly “line of site” between towers. But then, municipalities grew, and they needed more towers these towers were often not in site of one another, so the radio engineers started working with telecom companies and tying the LMR system to backhaul fiber solutions or LMR system access for management, the structure might look like this:
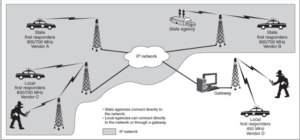
And here is where the fun begins!
I am assuming that many of my readers might be from smaller IT shops where you don’t have many assets to manage, if you are from a bigger network with a large IT department, I hope you are following these types of processes (If not, we need to talk!). Anyway, many of these smaller networks, in my experience, are not set up for multiple VLANS. Instead, they are flat networks where all the assets are on one default VLAN. This might be because the company has not invested in infrastructure, or the IT person doesn’t know how to set up VLANS (this situation is also common). So, let’s assume the scenario that your leaders came to you and said they want to be able to manage the LMR network from their computers instead of having to go onsite. If you have a flat network this means that those devices (repeaters, amplifiers, etc.) will now have an IP on your network. Should your network be compromised, the threat actor could in this case use known exploits against your LMR devices taking down a critical communication system (remember most likely your LMR is for security or fire or police and thus, critical). In this case, you want to create a VLAN that the LMR rides on and then set up ACL’s as to who and what ports can access the LMR VLAN. I could go into more detail but just think on this simple scenario and if you want to know more or maybe a couple ideas, again hit me up on LinkedIn or email me). I hope this gives you some ideas of what to think about if you must expand your LMR network or if you need to provide a way to manage your existing network.

